As a result of the attacks of September 11, 2001, a new focus on securing the Nation's infrastructure
brought about development of new risk analysis strategies and programs. In 2009, the water-sector standard,
AWWA/ANSI J100-10 Risk and Resilience Management of Water and Wastewater Systems was published. This standard is
different than other types of risk analysis due to the fact that it includes a "resilience" component.
This J100 approach to risk and resilience analysis is time consuming and calculation intensive.
As a result, Applied Engineering Management Corporation (AEM) took on the task of developing a program to
assist you in completing a thorough and complete analysis of your system. By using PARRE™, your team
will be able to complete the analysis in a timely manner and can be confident that your work will be
compliant with America's Water Infrastructure Act of 2018 (AWIA) regulations.
This document is intended to assist you in using PARRE™. Step by step instructions will walk you through
each step and ensure compliance with the J100-21. Please note that this document is to be used in conjunction
with the J100-21 standard and is not intended to replace it.
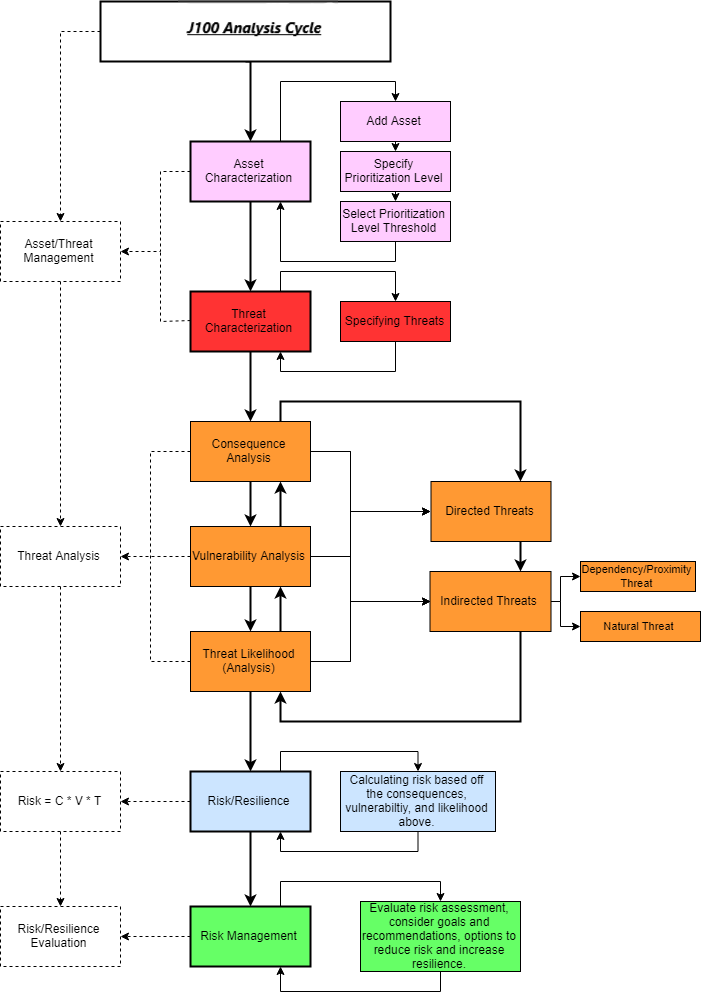 RAMCAP 7-Step Analysis Process
RAMCAP 7-Step Analysis Process
Upon arriving at the PARRE™ website, you will arrive at a screen prompting you to sign in. To get started, click Login
in the top left, or Here in the center of the screen.

A login screen will appear. Enter your email and password and click Log in. If it is your first time using the program, click the
Sign Up button to create your account.
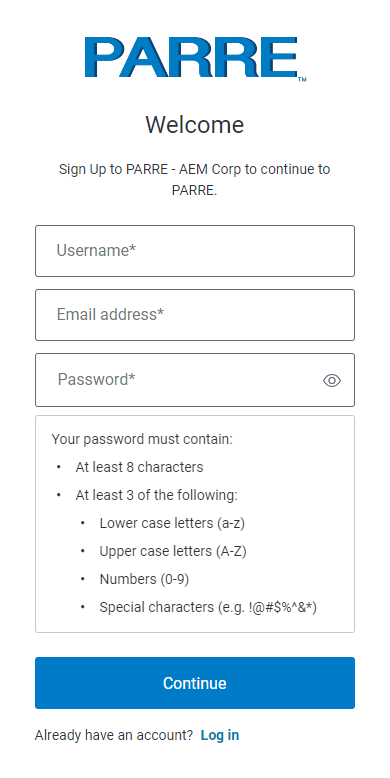
Create a username that you will remember for your PARRE login information. Then, input your email address that you want associated with your PARRE account. Lastly,
create a password that meets the requirements(at least 8 characters and at least three of the following: lower case letters (a-z), upper case letters (A-Z), numbers (0-9),
special characters (e.g. !@#$%^&*))
After successfully logging in, a welcome page will load, prompting you to open or create a new project. Click this button.
The website will direct you to a page showing all your existing projects.
Each information column can be filtered to sort all data by that specific column. Filter by clicking the white filter
icon

above the desired data column heading.
To add/change a filter, use the scroll tabs to find the desired filter. Each filter will display "items with value" that are in the scope of a specified filter.
To save the filter, press the orange filter box.
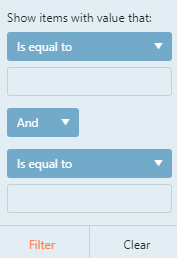
To cancel a filter, press clear. No information will be sorted.
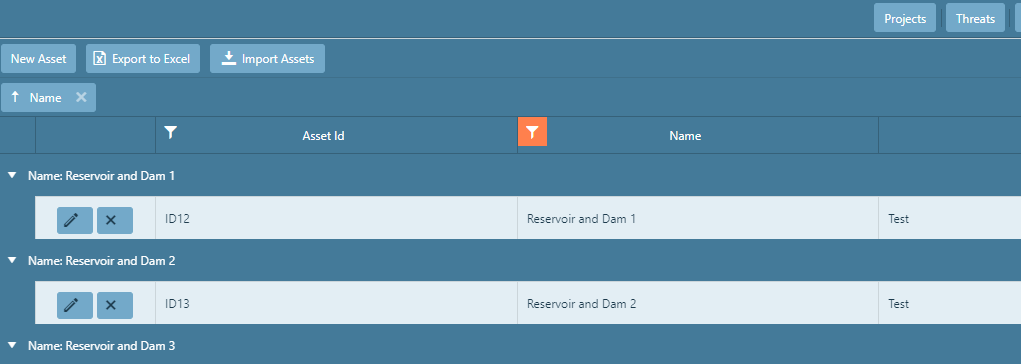
Any data column can be sorted by heading (e.g. Projects can be sorted by any column of category such as Name, Description, Address, etc). To group a column by category, click and hold the desired
category box. As you click and hold, an orange box will appear
with a symbol to the left of the name. Drag it over the Drag a column text
and release.


The symbol left of the name will change to when the hold can be
released over the text. A new box with the sorted column name will appear above the category boxes. The figure below is an example of sorting the projects page:
 |
 |
| Before dragging column header |
After dragging column header |
To undo a grouping, press the data box with the symbol (x) below New Project. This will return the page to its initial conditions.
Click the refresh button in the bottom right corner to refresh the page at any time.

To control how many line items are viewed on one page, click the box (bottom left) next to the left of items per page to view/specify other options.
By clicking the  button on the bottom of each page,
you will be directed to this User's Guide with instructions on how to complete each part of the analysis.
button on the bottom of each page,
you will be directed to this User's Guide with instructions on how to complete each part of the analysis.
To open an existing analysis that you have already created, click Open Project on the existing project you want to open.

This page also allows you to perform many tasks related to your projects. You may switch between analyses, edit basic
information about an analysis, share and remove read/write access to your projects with other users, create a new analysis, and delete
an analysis.
To create a new analysis, click New Project. See section Creating a New Project below for steps to creating a new analysis.
To edit the general information of an existing analysis, click the  edit button next to the desired analysis name from the
list.
edit button next to the desired analysis name from the
list.
To delete an existing analysis, select the desired analysis name from the list, and then click X.  Note: only project owners can delete a project.
Note: only project owners can delete a project.
Once you have logged in, you will be directed to the main projects page where you will be able to:
- View all your projects
- Create new projects
- Review, sort and edit previous projects
- Grant user access to your projects
To create a new analysis project, click the New Project  box found at the top left of the page.
box found at the top left of the page.
Once you have added a new project, a pop-up screen will appear. You will be directed to input the information displayed in the following figure. Please be aware that clicking
the Save box will save and close the project window.
Note: Project Name, Commodity Rate and Units are required inputs. The screen WILL NOT save without them.
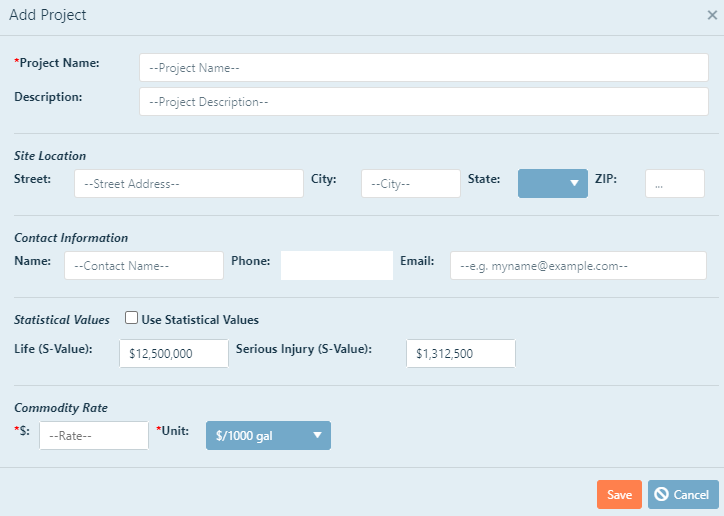
Project Name: In order to begin your analysis, you must give it a name. This is helpful for a few reasons:
- If you make a major mistake; you can create a new file and start over.
-
If you would like to create multiple analyses and have the ability to compare results;
you can switch between them at any time.
-
If you are planning on performing a PARRE™ analysis on multiple facilities and would like to store
them in their own files.
Choose a name that you are comfortable with.
It may be the name of the facility or asset to be analyzed, the date, or version number for example. Click inside the text box, and then type the desired name
Description: This is a more detailed description of the analysis. It is used to distinguish between
analyses that have similar names. You may add anything you would like to the description. Click inside the text box, and then type the desired description.
Site Location:The site location can be described multiple ways. It is typically the location of the main facility for the system being analyzed.
Add or edit the street, city, state, and zip code by clicking in the desired text box.
When finished, continue to the next box or click Save to close the window.
Contact Information:The contact person for the analysis should be the person that leads the effort and will have the most knowledge regarding the assessment if questions arise in the future.
Add or edit the name, phone number, and email address of the contact person by clicking in the desired text box. When
finished, continue to the next box or click Save to close the window.
Using Statistical Values: The statistical values of life and serious injury give a monetary value to a lost life and a serious injury.
If you choose not to use the statistical values of life and serious injury, leave the Statistical Values box unchecked.
If you chose to include statistical values of life, you have two choices; You may use the predetermined values given in the
program, which are the 2022 Department of Transportation (DOT) values, or you may provide your own values.
To include the statistical values of life and serious injury in your analysis, click the life s-value box.
To use your own values for Life (S-Value) and Serious Injury (S-Value), click inside the desired text box and type your desired
value in millions of dollars.
Commodity Rate:Commodity Rate is the price water is being sold to your customers. Add or edit the Commodity Rate and Units by clicking in the desired text box.
When finished, continue to another information box or click Save to close the window.
When all of the desired information above is entered, click Save. This action will save the entered data and close the window, returning to the main projects page.
To cancel the Project or edits, click Cancel. This action will close the window and return to the main projects page.
To import a backed up project from the legacy PARRE desktop application, in the Projects page click on the Import Project button next to the
'Project Access' button. This action with open the Import PARRE Project pop-up window.
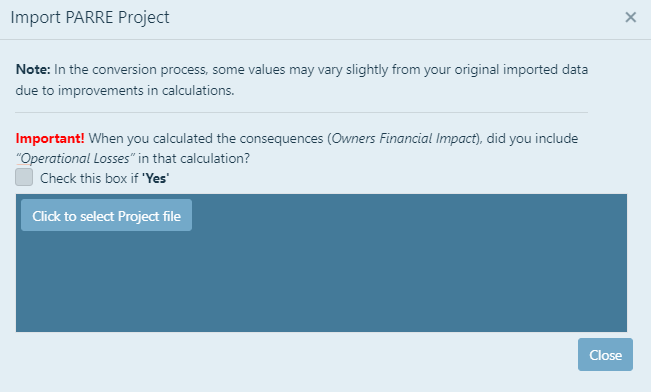
Note: In the conversion process, the "Natural hazards" values may vary slightly
from your original imported data.
If applicable, select the checkbox to answer the Important question regarding 'Owners Financial Impact' and 'Operational Losses', then click on the
Click to select Project file button. This action will allow you to select a PARRE backup file in a '.json' format. Once you have made a selection
click on the Open buttonn to add the file to the 'Import PARRE Project' window. Click on the Click to Import button to start the import process.
Note: Only PARRE backup files in .Json format are used to restore legacy project data.
Once the Click to Import button is clicked, you will be presented with a pop-up message window. This window displays a message stating that the restoration
of the legacy project will be performed in the background.
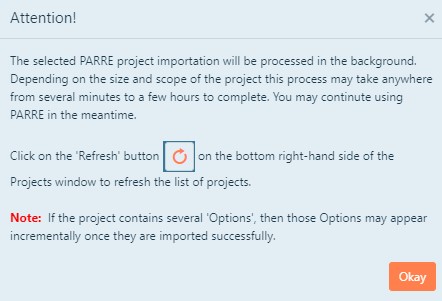
If the selected legacy project has been successfully queued as a background process a Queued Successfully pop-up message will appear. Otherwise, an error message will
be displayed. NOTE: Importing may take several minutes depending on the size of the file. Refresh screen to see newly imported projects.
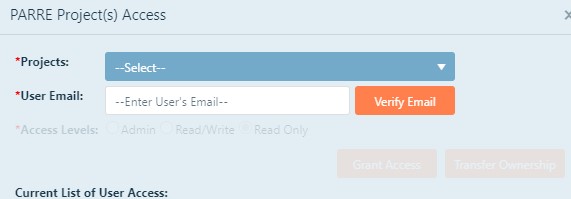
To add or remove user access from your projects, go to the Projects page and click Project Access next to the New Project button.
Select the project you want to give access to from the drop down menu and add the users email. Click Verify Email to confirm
the user is in the system. Then, select the level of access you want to give, and then click Grant Access.
Click the Close button to close this screen.
- Read/Write - Provides users the ability to view as well as edit the selected project.
- Read Only - Provides users the ability to view the selected project
- Admin - Provides users the ability to view/edit the project as well as delete and grant access.






 button on the bottom of each page,
you will be directed to this User's Guide with instructions on how to complete each part of the analysis.
button on the bottom of each page,
you will be directed to this User's Guide with instructions on how to complete each part of the analysis.
 Note: only project owners can delete a project.
Note: only project owners can delete a project.


